For Caitlin Clark, every day with Connor McCaffery feels like a three pointer. Hot off a record-breaking performance in the NCAA women’s tournament, Caitlin
TECHNOLOGY

Chilean instant payments API startup Fintoc raises $7 million to turn Mexico into its main market
Open banking may be a global trend, but implementation is fragmented. The fintech startups doing the legwork to make it
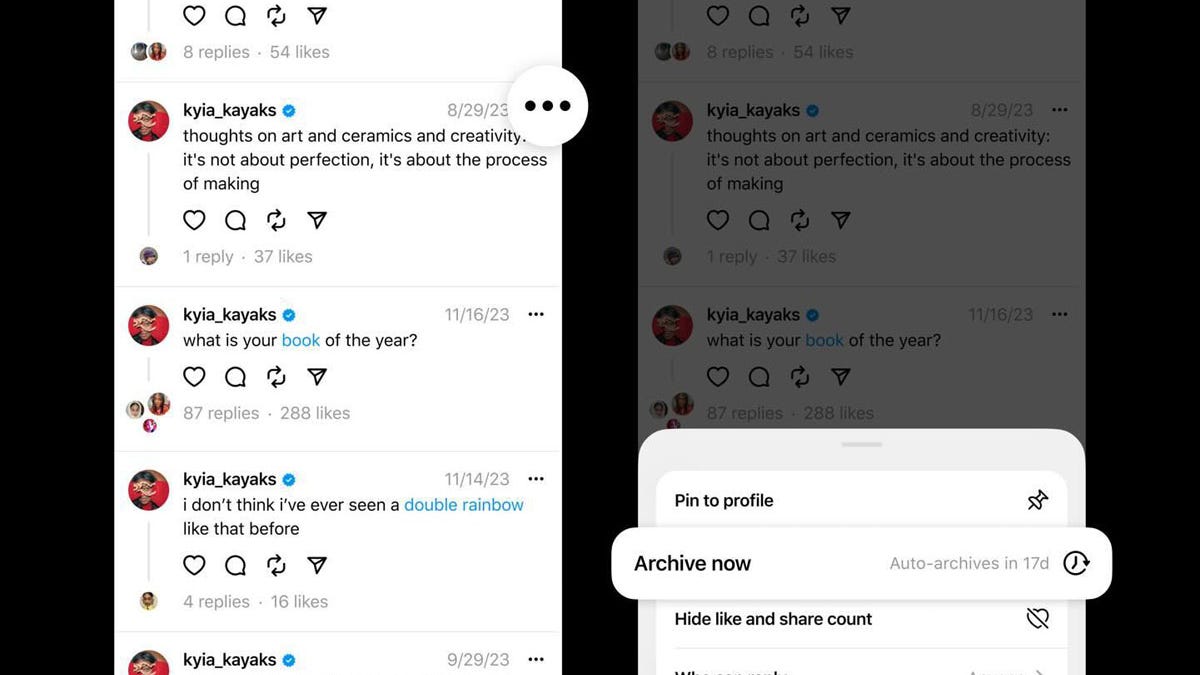
Threads tests letting you hide your public posts, as monthly users jump to over 150 million
Lance Whitney/ZDNET Meta is testing a new Threads feature that lets you archive your public posts, rendering them invisible to

Ex-NSA hacker and ex-Apple researcher launch startup to protect Apple devices
Two veteran security experts are launching a startup that aims to help other makers of cybersecurity products to up their
7 reasons I use Copilot instead of ChatGPT
Sabrina Ortiz/ZDNET The launch of OpenAI’s ChatGPT kicked off the generative AI craze and the tool has remained the most

TikTok pulls feature from Lite app in EU over addiction concerns
TikTok suspended a gamification feature in the European Union following an intervention by the bloc. With attention on TikTok’s growing
World

‘Create harmony’: Q&A with China’s Foreign Minister Wang Yi | Israel War on Gaza News
In an interview with Al Jazeera, Chinese Foreign Minister Wang Yi stressed the need to correct what he described as













