Keeping up with an industry as fast-moving as AI is a tall order. So until an AI can do it for you,
LATEST NEWS
TECHNOLOGY

This Week in AI: When ‘open source’ isn’t so open
Keeping up with an industry as fast-moving as AI is a tall order. So until an AI can do it for you,
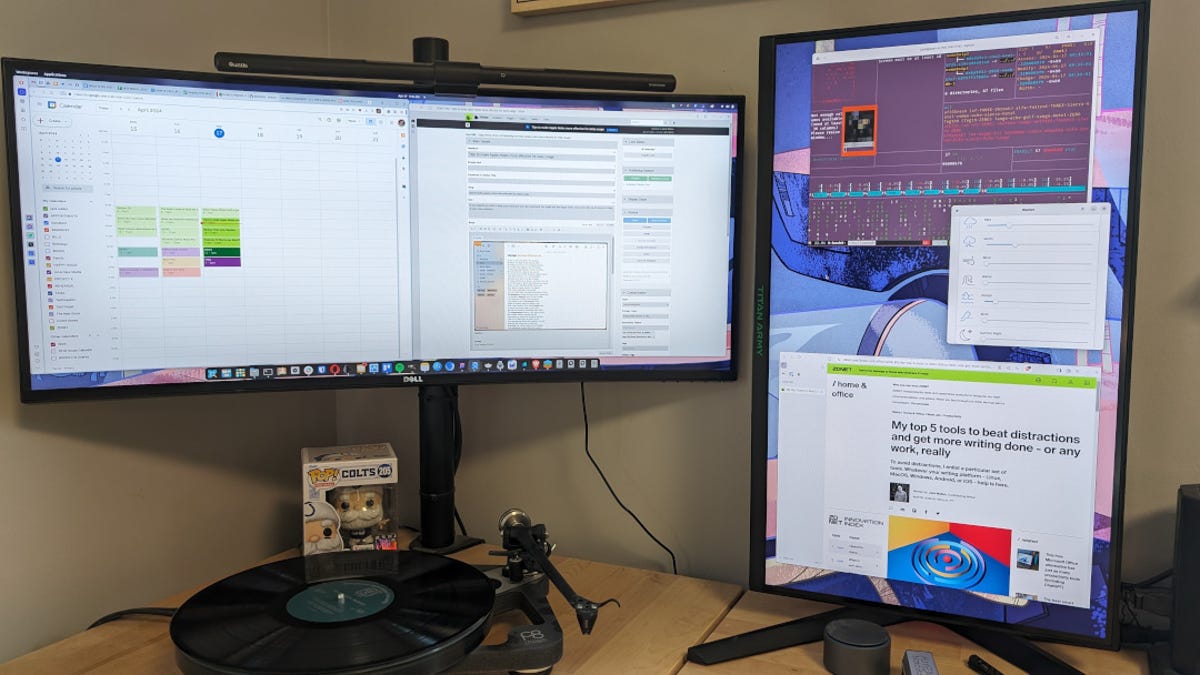
How I turned a cheap gaming monitor into the ultimate productivity tool
Jack Wallen/ZDNET ZDNET’s key takeaways The Titan Army 27″ gaming monitor is available on Amazon for $200. This monitor makes
CesiumAstro claims former exec spilled trade secrets to upstart competitor AnySignal
CesiumAstro alleges in a newly filed lawsuit that a former executive disclosed trade secrets and confidential information about sensitive tech,

Your Android phone could have stalkerware — here’s how to remove it
Consumer-grade spyware apps that covertly and continually monitor your private messages, photos, phone calls and real-time location are a growing
Too many models | TechCrunch
How many AI models is too many? It depends on how you look at it, but 10 a week is
World

UK returns looted Ghana artefacts on loan after 150 years | Arts and Culture News
The objects were stolen from the court of the Asante king during the 19th century Anglo-Asante wars. The United Kingdom














