A New York appeals court has overturned Harvey Weinstein’s 2020 conviction for rape, saying the trial judge should not have
TECHNOLOGY

Zomato’s quick commerce unit Blinkit eclipses core food business in value, says Goldman Sachs
Goldman Sachs said in a report late Thursday that Indian food delivery giant Zomato’s quick commerce arm Blinkit is now

The FTC’s ban on noncompete clauses could be good for startups. But it also might be struck down.
The Federal Trade Commission voted 3-2 to ban the use of most noncompete agreements on Tuesday. This ruling means companies

How to change your IP address, why you’d want to – and when you shouldn’t
Jack Wallen/ZDNET Security and privacy have been hot topics for a long time (and that’s not going to change any

Snap says total watch time on its TikTok competitor increased more than 125%
As part of its Q1 2024 earning release, Snap revealed that total watch time on its TikTok competitor, Spotlight, increased
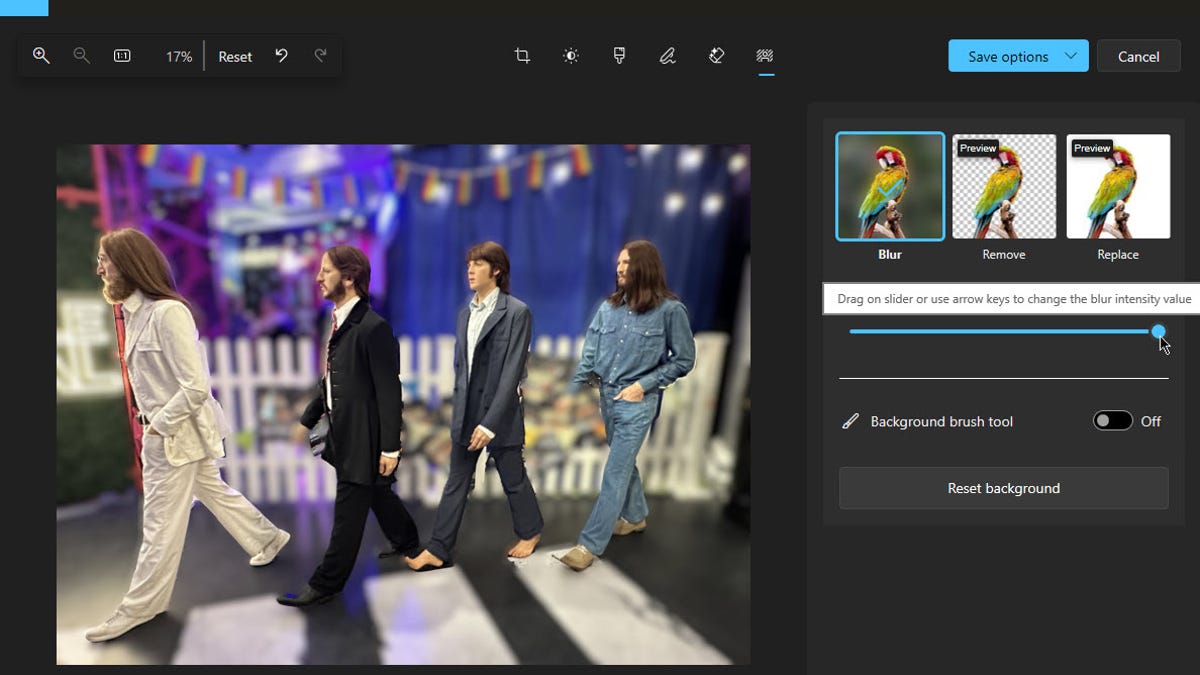
How to use AI in the Windows Photos app to change the background of an image
Screenshot by Lance Whitney/ZDNET You’ve snapped a memorable photo with your phone. There’s only one problem — you don’t like
World

‘Profoundly unjust’: Reactions to court overturning Weinstein’s conviction | Sexual Assault News
A New York appeals court has overturned Harvey Weinstein’s 2020 conviction for rape, saying the trial judge should not have